
Vulnerability Management
Vulnerabilities exist.
The challenge is knowing what to fix, when, and by whom
Companies deal daily with hundreds of vulnerabilities coming from scanners, tests, and dependencies. We help turn volume into priority by creating control, predictability, and traceability throughout the remediation lifecycle.

More testing, more alerts, and less clarity
As AppSec matures, organizations adopt more tools, more automated testing, and generate more data. SAST, DAST, SCA, penetration testing, and infrastructure scanners now run continuously. The problem is that vulnerability volume has grown faster than management capacity.
Today, companies commonly face:
Large, outdated backlogs
Difficulty working with development teams on remediation
Generic severity ratings without environmental context
Inconsistent remediation approaches across squads and projects
Duplicate vulnerabilities from different sources
No clear ownership per application or vulnerability
Slow fixes with no traceability
Audits based on spreadsheets and manual evidence collection
A segurança que acompanha o ritmo da sua fintech
Unimos tecnologia, inteligência e consultoria Combinamos tecnologia, inteligência e consultoria para transformar vulnerabilidades em eficiência e conformidade contínua.para transformar vulnerabilidades em confiança e compliance contínuo.
Modern environments receive findings from multiple sources: code scanners, dynamic testing, dependency analysis, and manual testing. Without a central point of control, this information becomes fragmented.
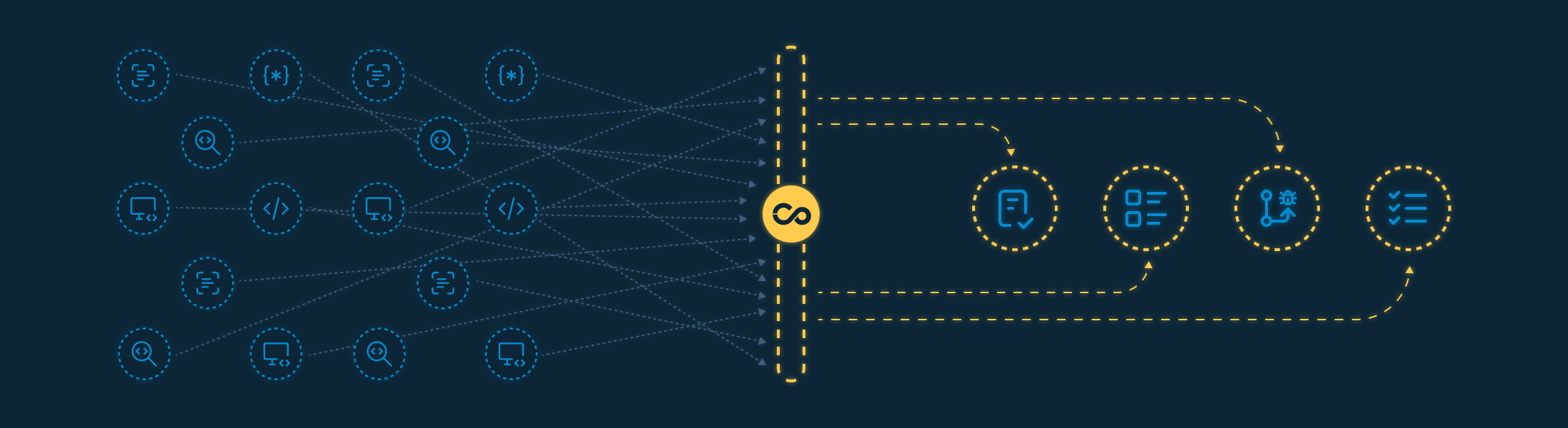
How we organize this scenario

Consolidation of technical findings into a single backlog

Correlation and deduplication across different sources

Complete history per application, vulnerability, and remediation cycle
Direct impact on your operation

Reliable prioritization based on real risk volume
.svg)
Significant reduction in operational noise and rework

An actionable backlog focused on vulnerabilities that truly matter
Severity alone does not define priority. A critical flaw in an isolated system has a different impact than a medium vulnerability in an exposed API.
How we prioritize correctly

Classification based on application criticality

Exposure analysis (internet-facing, APIs, integrations)

Technical and environmental context

Alignment with regulatory requirements
Direct impact on your operation

Focus on what truly represents risk

Reduction of unnecessary remediation efforts

Better use of engineering time
Vulnerabilities without owners do not get fixed. Effective management requires clear accountability and tracking.
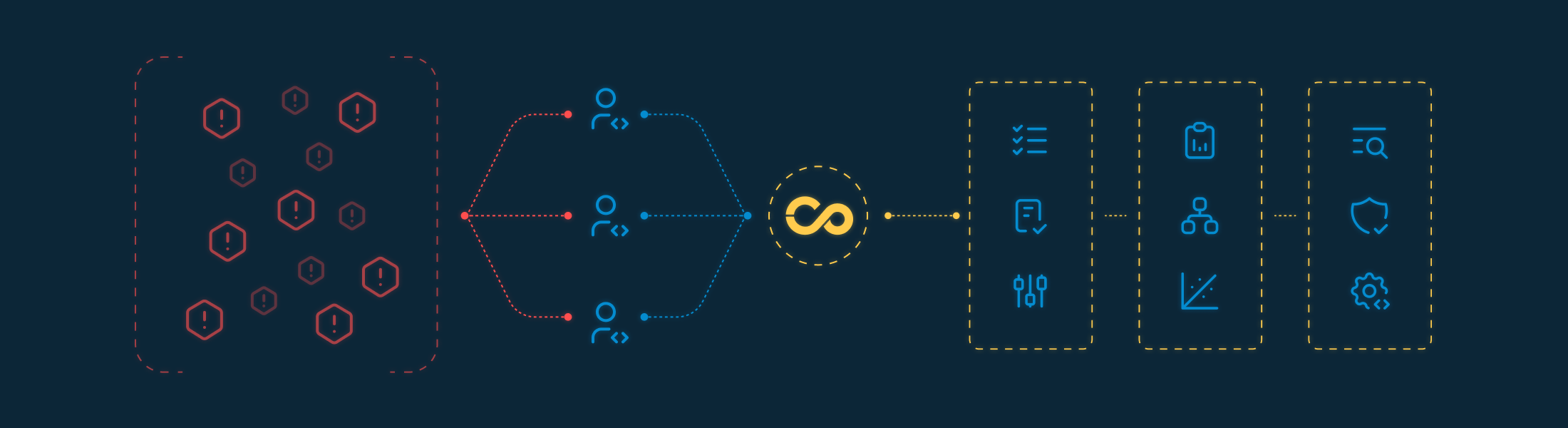
How we structure the workflow

Defined owners per application and per vulnerability

Integration with development tools

SLA tracking and remediation time monitoring

Status visibility: open, in progress, resolved, accepted
Direct impact on your operation

Fewer forgotten vulnerabilities

More predictable remediation cycles

Stronger alignment between security and engineering
A significant portion of vulnerabilities today originate not in proprietary code, but in third-party libraries and components.
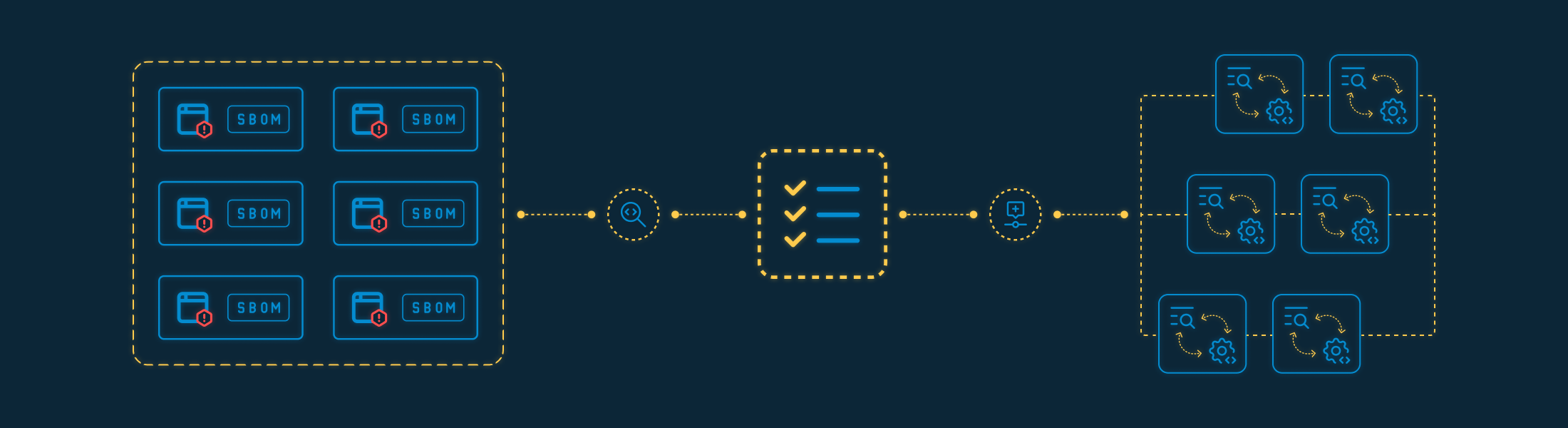
How we address this risk

SBOM generation per application

Identification of CVEs in open-source dependencies

Traceability of where each vulnerable component is used

Continuous remediation tracking
Direct impact on your operation

Real visibility into the attack surface

Reduced inherited exposure from third parties

Ongoing control of the software supply chain
Vulnerability management must also support audits, internal requirements, and regulatory standards.
How we build governance

Historical records of findings and remediation

Evidence organized by application and time period

Trend and evolution metrics

Traceability between vulnerability, action, and responsible party
Direct impact on your operation

More predictable audits

Reduced effort in evidence collection

Security operating as a continuous process
Vulnerability management with context and risk focus
Since 2008, we have supported companies in building application security programs that work in real-world operations. Our approach connects technology, process, and people to manage vulnerabilities with context and predictability.
Operational risk-driven prioritization considering application criticality, exposure, and usage context
.svg)
Management model applied in regulated and critical environments, focused on predictability, traceability, and governance
Continuous vulnerability lifecycle management, from identification to closure, with long-term tracking
Integration into the development workflow, connecting vulnerabilities, remediation, and risk SLAs
Talk to our specialists and see how to structure a continuous process with less noise and more control.
