
AppSec AI Agent
Artificial Intelligence Specialized in AppSec
We accelerate and scale the development of secure applications with a specialized AI agent that operates continuously, autonomously, and integrated into the development cycle—delivering diagnostics, fixes, and seamless support for the development team.
A inteligência artificial certa, no lugar certo e na hora certa
AppSec AI Agent atua onde a segurança realmente precisa acontecer: dentro do código, no pull request, no pipeline e na governança.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Suspendisse varius enim in eros elementum tristique. Duis cursus, mi quis viverra ornare, eros dolor interdum nulla, ut commodo diam libero vitae erat. Aenean faucibus nibh et justo cursus id rutrum lorem imperdiet. Nunc ut sem vitae risus tristique posuere.



Agente de diagnóstico
Analisa continuamente dados de ferramentas de AppSec e pipelines de CI/CD. Correlaciona resultados de SAST, DAST, SCA e sinais contextuais para priorizar riscos com base em impacto, exposição e criticidade.


Agente de correção
Apoia os desenvolvedores na remediação, oferecendo sugestões de correção específicas e referências técnicas confiáveis, diretamente integradas ao fluxo de trabalho.




Agente de revisão de código
Executa revisões automatizadas de pull requests, identificando código inseguro e violações de políticas definidas, com feedback claro e imediato.


Agente de Threat Modeling
Gera e mantém modelos de ameaça atualizados a partir da análise de arquiteturas, fluxos e superfícies de ataque. Fornece visualizações práticas para orientar decisões de segurança desde as fases iniciais de desenvolvimento.




Agente de acompanhamento
Monitora a execução das ações de AppSec, acompanha o status das vulnerabilidades, envia alertas em tempo real e valida a aplicação de correções.


Agente de capacitação
Atua como mentor inteligente dentro da IDE. Explica vulnerabilidades, sugere correções seguras e conecta os desenvolvedores a conteúdos educativos, apoiando programas de Security Champions e promovendo aprendizado contínuo.

The right artificial intelligence, in the right place, at the right time.
The AppSec AI Agent operates where security truly matters: in the code, in pull requests, within the pipeline, and across governance processes.

Smart diagnostic
Continuously analyzes AppSec tools and CI/CD pipeline data. Correlates SAST, DAST, SCA results, and contextual signals to prioritize risks based on impact, exposure, and severity.

Suggested corrections
Assists developers with remediation by providing precise fix suggestions and reliable technical references, directly embedded into the workflow.

Automated code review
Performs automated pull request reviews, identifying insecure code and policy violations, with clear and immediate feedback.

Threat Modeling Agent
Automatically creates and maintains updated threat models by analyzing architectures, flows, and attack surfaces. Provides practical visualizations to guide early-stage security decisions.

Remediation Agent
Tracks the execution of AppSec actions, monitors vulnerability status, sends real-time alerts, and validates remediation efforts.

Continuous enablemnet
Acts as an intelligent mentor within the IDE. Explains vulnerabilities, recommends secure fixes, and links developers to educational content — supporting Security Champions programs and continuous learning.
Training Agent
AI specialized in AppSec, acting as a technical mentor inside the IDE — guiding developers with suggestions, explanations, and educational content as they write code.
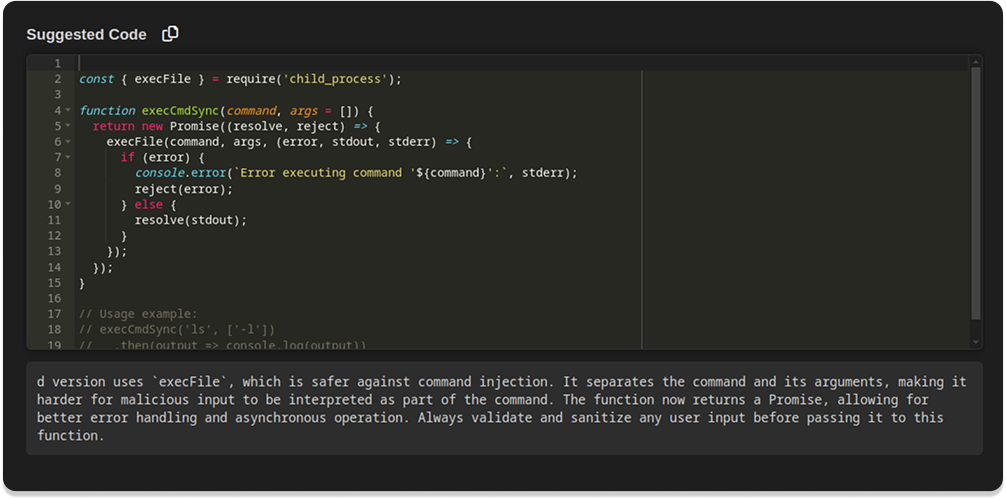
Contextual fix suggestions and technical insights directly in the IDE, without disrupting the developer’s flow.
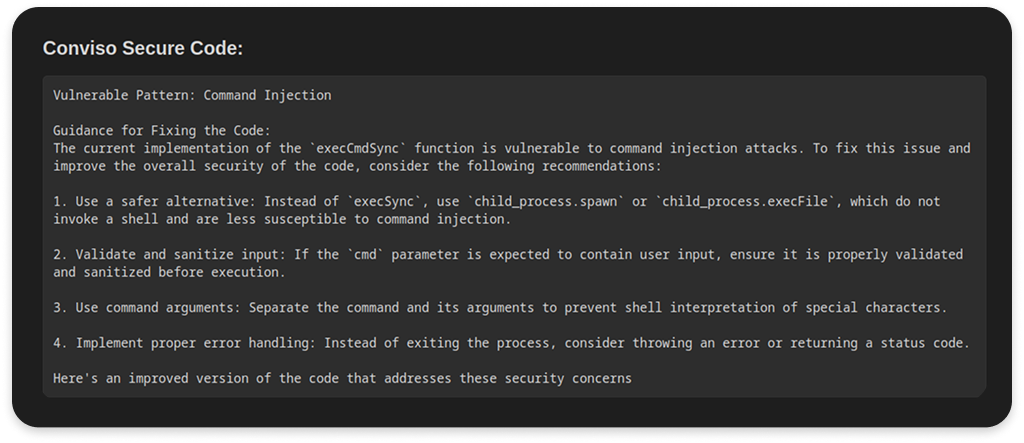
Each issue comes with a detailed technical analysis, organized by frequency across the team.
Articles, documentation, and news linked to the specific vulnerability — reinforcing hands-on learning within the IDE.
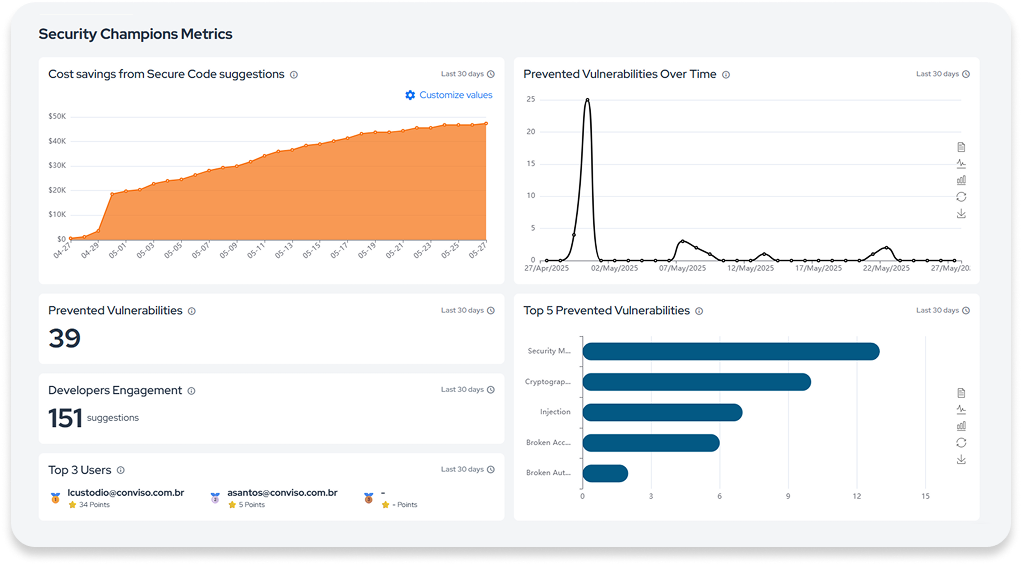
Includes data like prevented vulnerabilities, top-engaged developers, most resolved issues, filters by date, and cost savings.
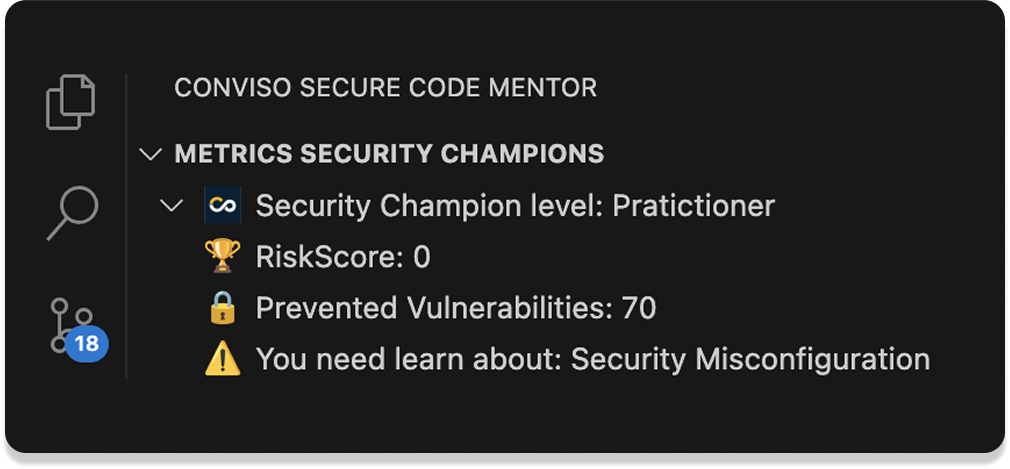
Tracks technical progress, participation in fixes, and content engagement to identify and develop security leaders.
Scale AppSec with an AI agent in the development workflow


Secure development from the start

Integrated security across development
.svg)
Continuous enablement

Reduced time and rework

Operational efficiency and cost reduction

Scalable for large teams

Contextual tntelligence

Governance, compliance, and contextual intelligence

Threat modeling

Intelligent agent that provides diagnostics and fixes without relying on manual services.

Specialized knowledge base
Agent trained with real-world data and patterns from AppSec experts with over 17 years of experience.
Agent trained with real-world data and patterns from AppSec experts with over 17 years of experience.
.svg)
Specialized artificial intelligenceAI applied for contextual analysis, risk prioritization, and autonomous, continuous correction recommendations.

Dev-First approach
Seamlessly integrates with existing developer tools (IDEs, Git, CI/CD), placing Devs at the center with contextual feedback within their workflow.
Seamlessly integrates with existing developer tools (IDEs, Git, CI/CD), placing Devs at the center with contextual feedback within their workflow.
.svg)
Native integration with Conviso Platform
Consolidates agent data, correlates detected and resolved vulnerabilities, connects to pipelines and repositories, and provides real-time visibility of its activity within the development cycle.
Consolidates agent data, correlates detected and resolved vulnerabilities, connects to pipelines and repositories, and provides real-time visibility of its activity within the development cycle.
.svg)
Expert validationConviso specialists validate and oversee the work of the AI agent as an additional layer of technical control.

Automatic PR validation with trained AIActs proactively on pull requests, analyzing code whenever a developer opens one. Identifies vulnerable code segments, suggests secure fixes, and automatically generates a new commit.

Integrate the AI agent into your development pipeline and scale your security autonomously
 Free trial
Free trialTalk to our experts
Talk to our team and learn how to use our agent in your secure development process.
Oops! Something went wrong while submitting the form.





