
Application Security Testing
Security testing is mandatory. Scaling AST is the real challenge.
Companies are running more security tests across the SDLC than ever before, but struggle to organize results, prioritize remediation, and integrate execution into development workflows.

More tests distributed across the SDLC
The evolution of DevSecOps practices has expanded the use of SAST, DAST, IAST, SCA, secrets scanning, and manual validations across multiple phases of the development lifecycle. These tests now run continuously — in pipelines, test environments, staging, and production. The challenge is no longer executing tests. The challenge is operating this entire testing ecosystem as a unified system.
Today, companies face:
Lack of correlation between findings identified by different testing techniques
Inconsistent remediation practices across teams
Generic severity ratings without application or environmental context
Low visibility into actual test coverage
Limited integration with development workflows
Recurring execution without consolidated historical tracking
Security test and scan results scattered across tools, squads, and pipelines
A segurança que acompanha o ritmo da sua fintech
Unimos tecnologia, inteligência e consultoria Combinamos tecnologia, inteligência e consultoria para transformar vulnerabilidades em eficiência e conformidade contínua.para transformar vulnerabilidades em confiança e compliance contínuo.
Security testing does not work in isolation. Different testing techniques cover distinct parts of the attack surface, at different SDLC stages, each with inherent limitations. The real value emerges when these executions are orchestrated, correlated, and treated as a unified system.
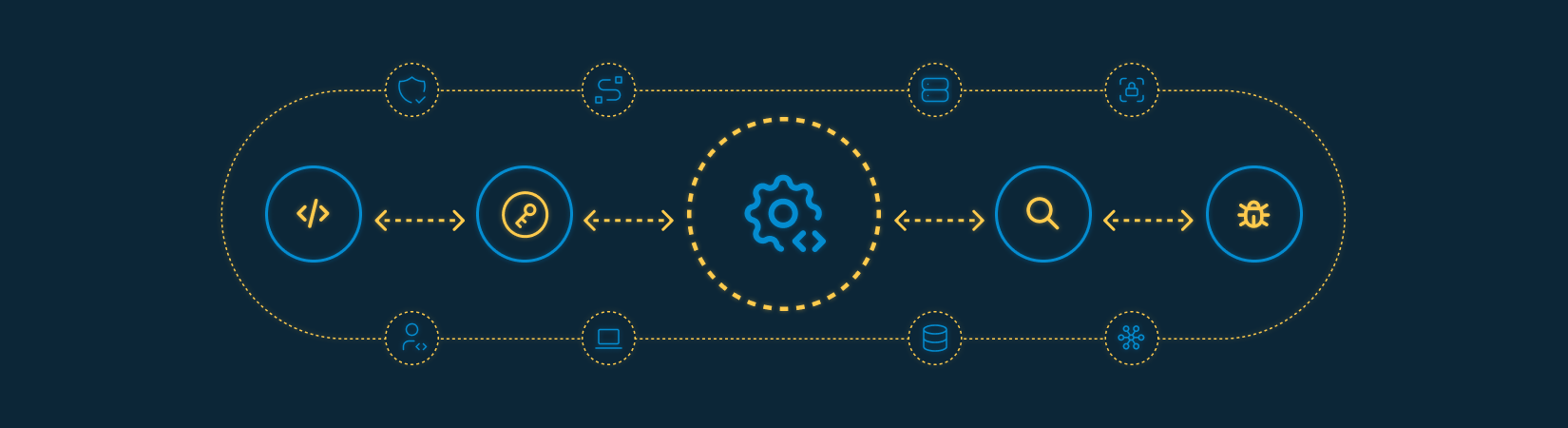
How we structure the testing lifecycle:

SAST to identify source code flaws early in development

Secrets Scanning to detect exposed credentials, keys, tokens, and secrets in code, repositories, pipelines, and artifacts

SCA to identify vulnerabilities in libraries and dependencies

DAST to test running applications and APIs
Direct impact on your operation
.svg)
Broader attack surface coverage

Reduced gaps between SDLC phases

More efficient use of each testing technique at the right moment

Less reliance on reactive, one-off execution
Modern environments receive findings from multiple sources: static scanners, dynamic tests, dependency analysis, and manual validations. Without a central control point, this data quickly becomes fragmented.
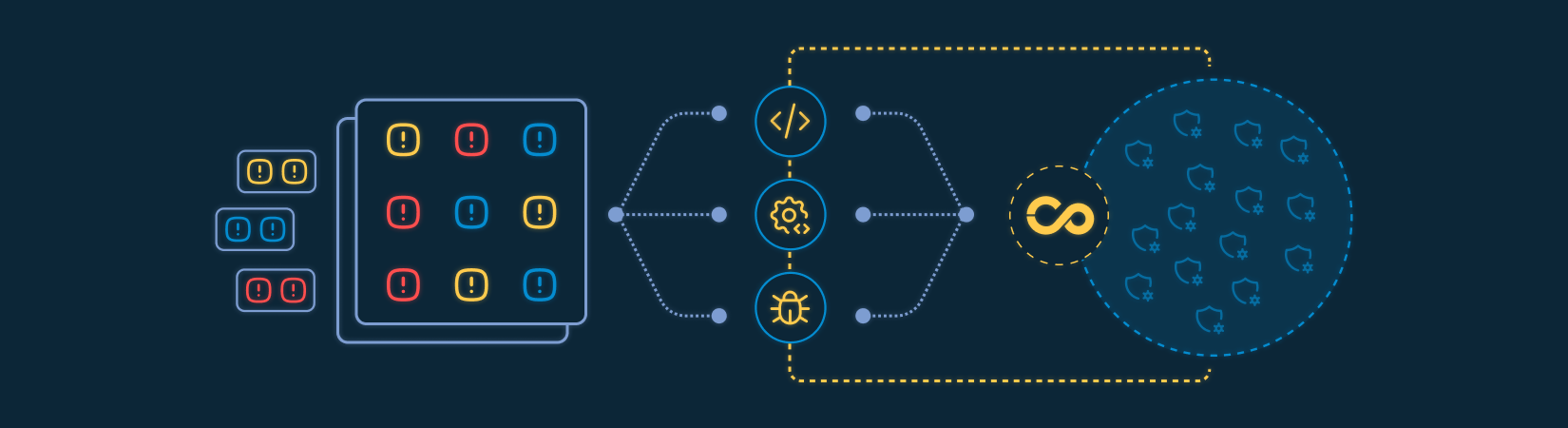
How we organize this scenario:

Consolidation of findings into a single security backlog

Correlation and deduplication across different testing techniques

Organization by application, environment, vulnerability type, and criticality

Complete history per vulnerability, including retesting and remediation cycles
Direct impact on your operation

Reduced operational noise and rework between teams
.svg)
A consistent and continuously updated backlog

Clear visibility into the real volume of vulnerabilities

Strong foundation for prioritization and decision-making
Security testing only scales when it keeps pace with engineering. Executions outside the development flow create friction, delays, and resistance.
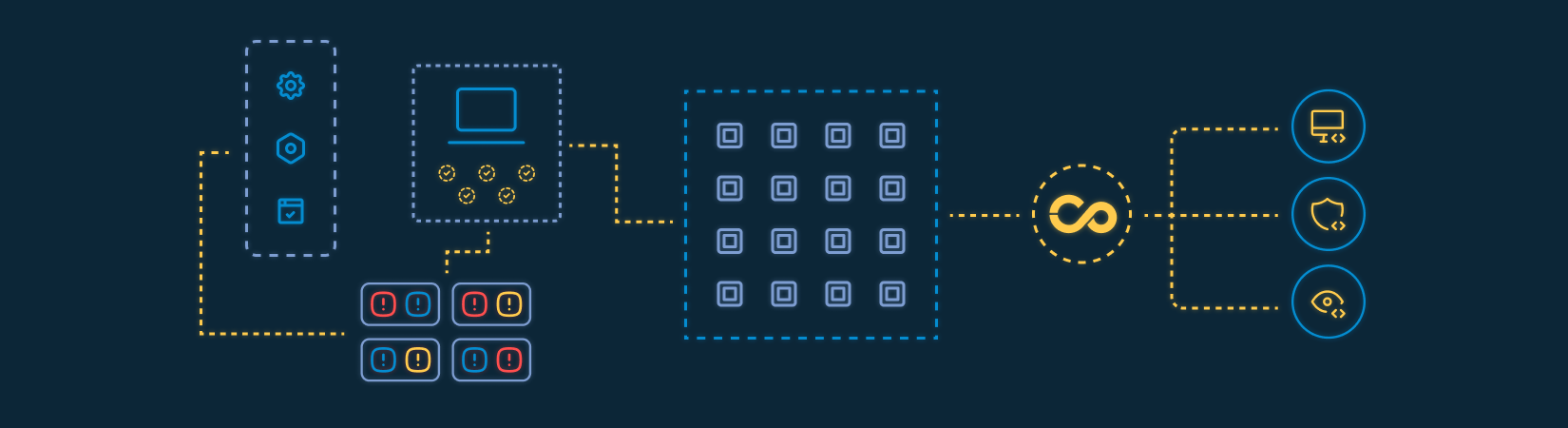
How we connect testing to the SDLC

Automated test execution within CI/CD pipelines

Definition of security gates based on objective technical criteria

Integration with issue tracking and backlog management tools

Structured technical feedback delivered directly to development teams
Direct impact on your operation

Reduced friction between security and engineering
.svg)
Earlier and lower-cost remediation

Fewer vulnerabilities reaching production

Security embedded in the process — not added at the end
Security testing generates volume. Priority does not come solely from tool-assigned severity, but from real application context.
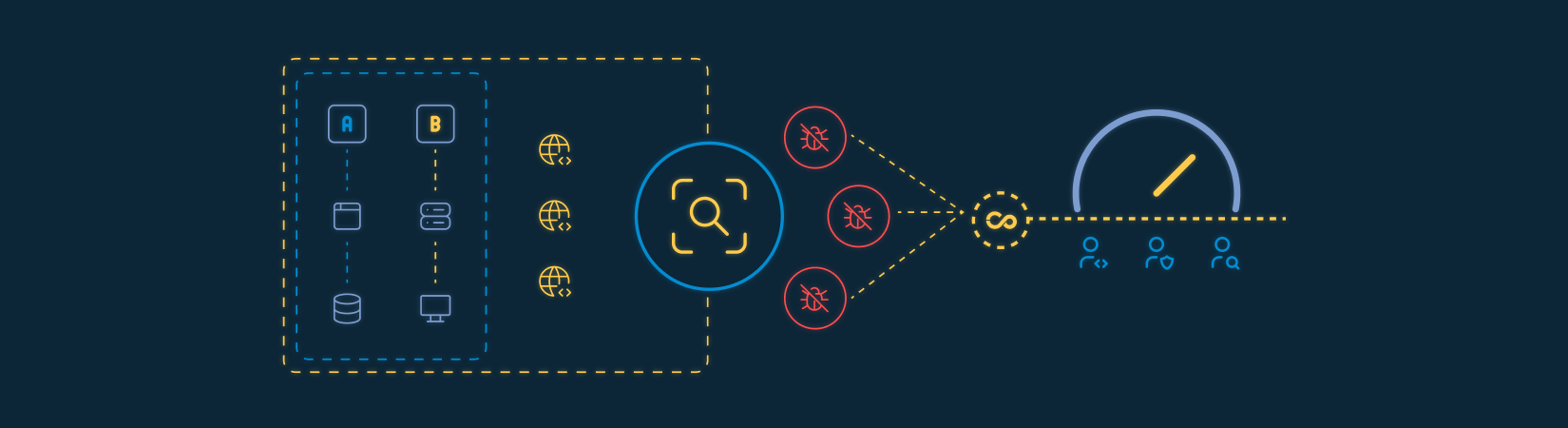
How we structure prioritization

Relationship between vulnerability, application, environment, and exposure

Differentiation between theoretical findings and exploitable risks

Combined assessment of technical, operational, and regulatory impact

Unified visibility for AppSec, Engineering, and Management
Direct impact on your operation
.svg)
Teams focus on what truly reduces risk
.svg)
Less time spent on low-impact vulnerabilities

Better use of squad remediation capacity

Decisions based on real risk, not just technical scoring
Security testing is not a one-time event — it is a continuous process that must be measured, monitored, and refined over time.
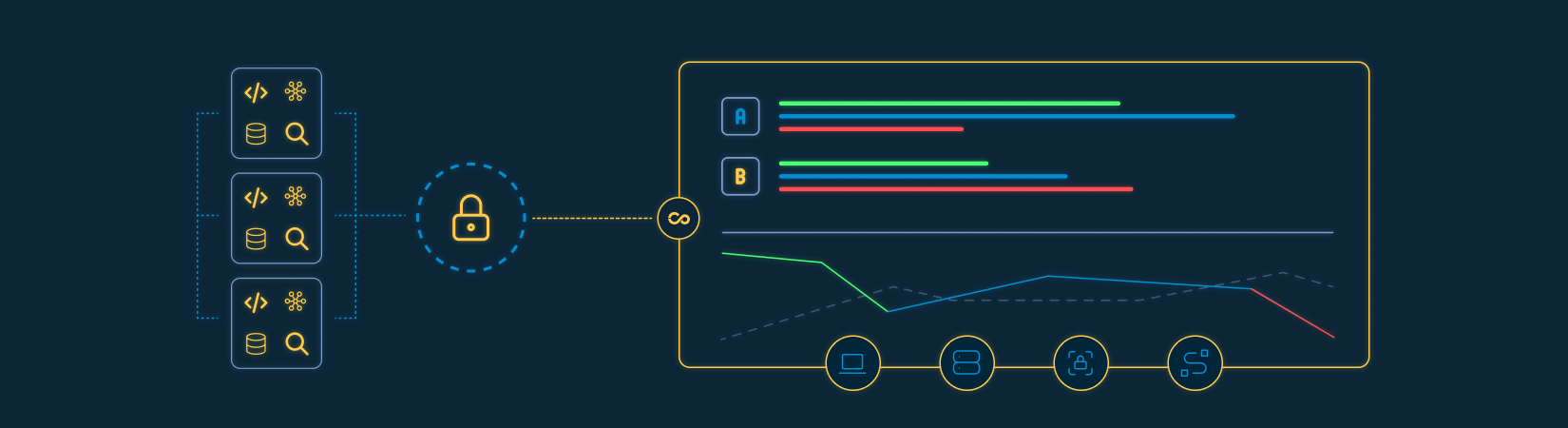
How we measure maturity and evolution

Clear visibility into which applications are being tested

Types of tests executed per application and environment

Execution frequency throughout the SDLC

Findings evolution, remediation rates, and recurrence
Impacto direto para sua operação

Clear understanding of real AppSec maturity

Identification of coverage gaps and redundant testing

Objective tracking of risk evolution over time

Concrete foundation for strategic security investments
Risk-driven orchestration and consolidated management
Since 2008, Conviso has operated application security programs aligned with real-world SDLCs, connecting test execution, result management, and remediation workflows.
Unified orchestration of AST techniques, with normalization and correlation in a single management flow
.svg)
Structured treatment of findings focused on clarity and actionability for engineering teams
AST fully integrated into the application lifecycle, tracking risk evolution across the SDLC
A platform built for scale, supporting complex and distributed environments
Talk to our specialists and discover how to structure security testing in a continuous, integrated, and manageable way.
