PLATFORM OVERVIEW
Continuous evolution in AppSec, aligned with your business maturity
Conviso Platform is an ASPM platform that integrates security into the real development cycle and centralizes AppSec processes in a modular, scalable way, tailored to the maturity of your business.

Everything your AppSec program needs. In one place.
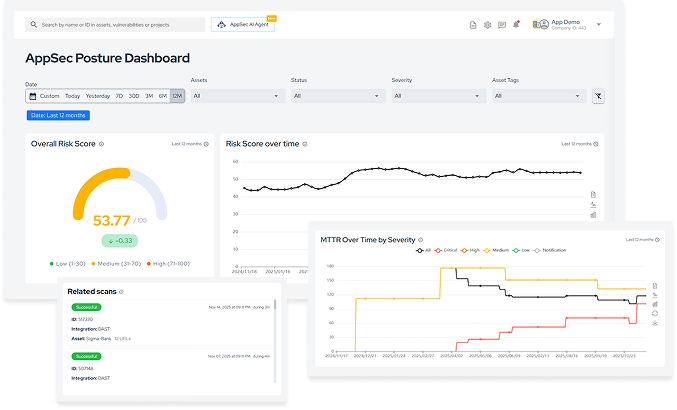
Centralizes and correlates security data for managing application posture, with full visibility through dashboards, metrics, and traceability to monitor risk, maturity, and compliance with your AppSec program.


.svg)






.svg)
Continuous, automated security built for developers
.png)
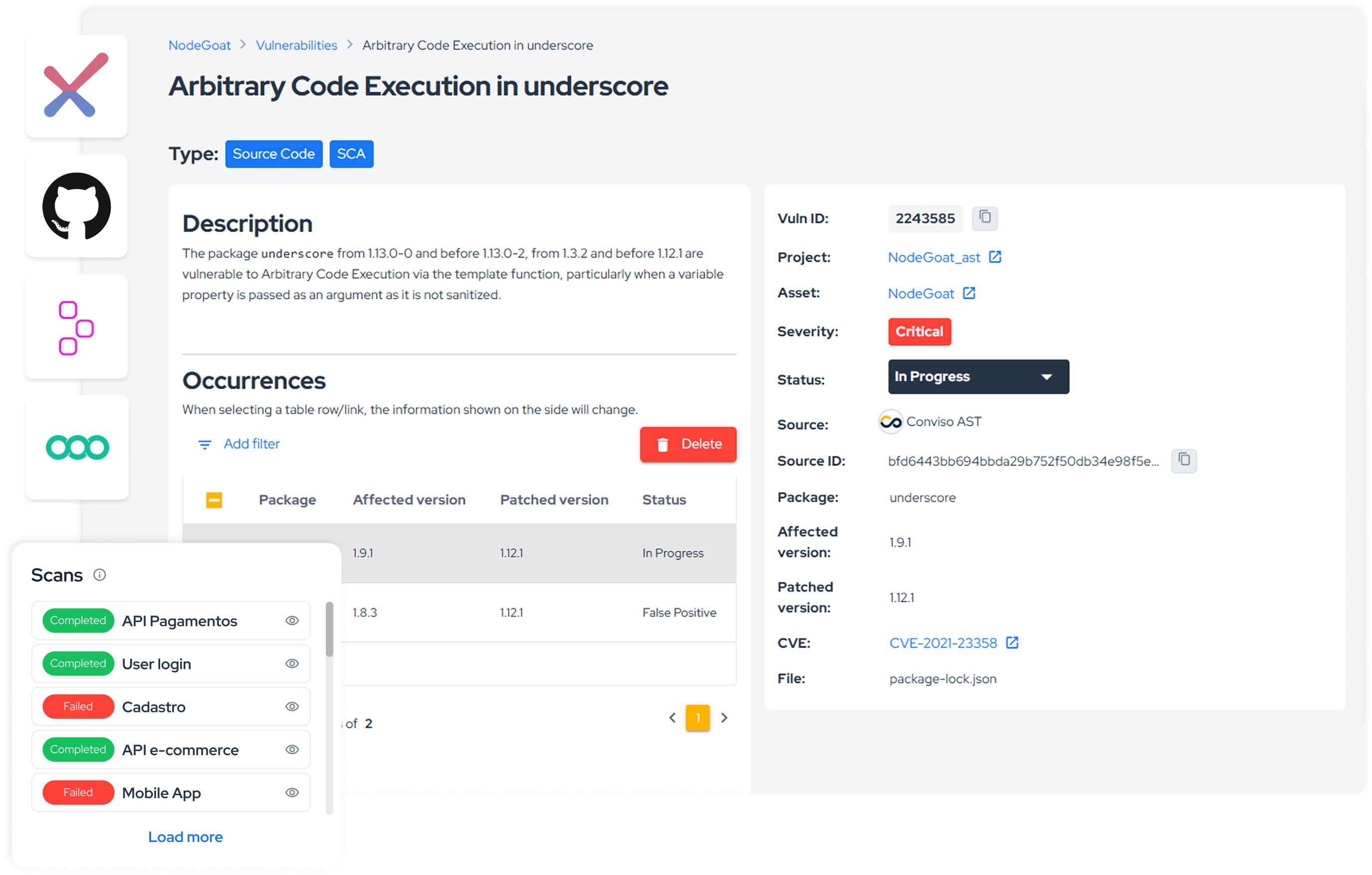
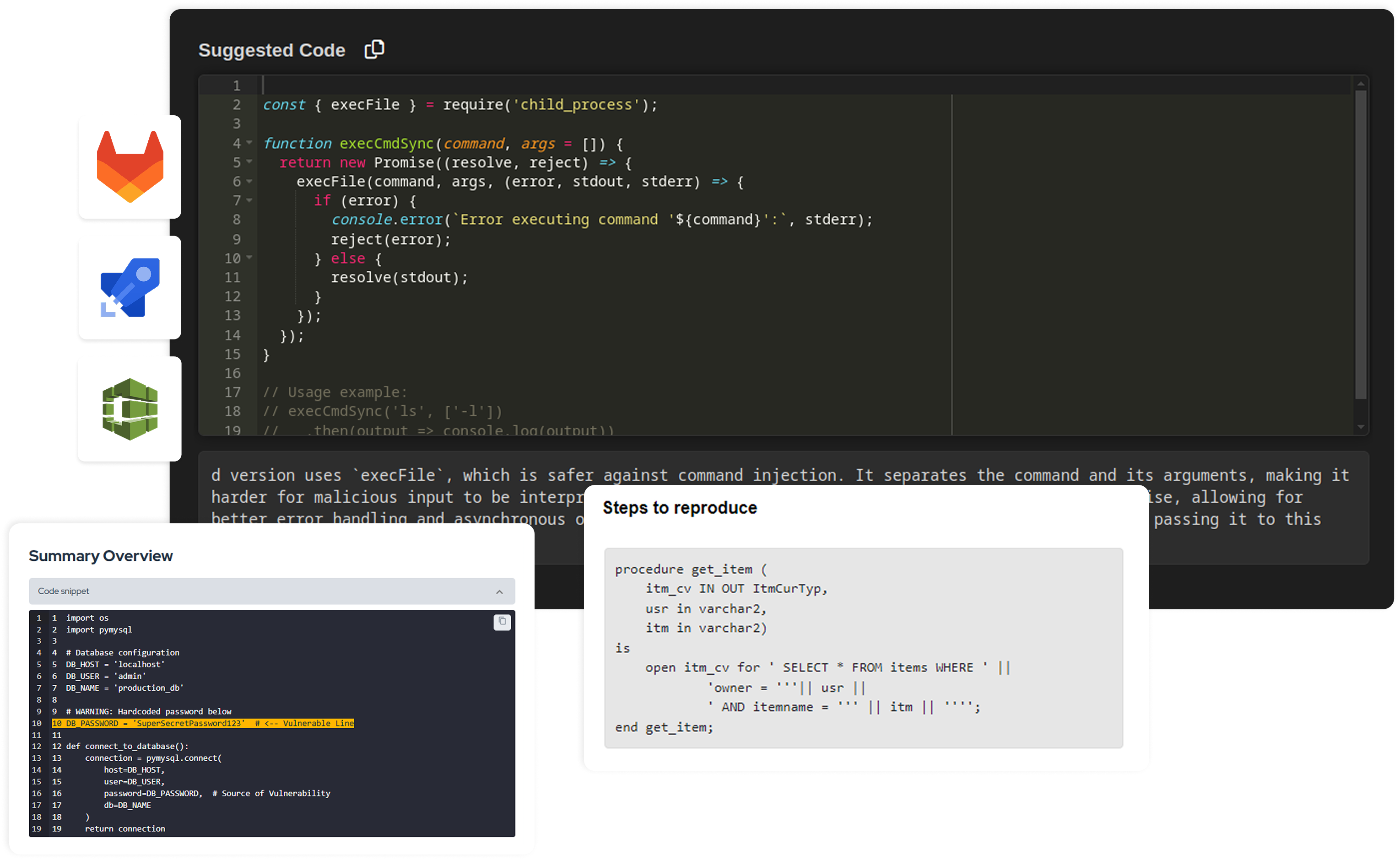
.png)

Continuous, automated security built for developers
.png)



.png)

Intelligent, integrated, and continuous AppSec

Features developed based on real-world risks and key AppSec trends.

Activates only what makes sense for your company’s maturity level.

Embeds security into the developer workflow without friction or disrupting daily routines.

Security applied from the beginning of the development cycle to build secure software from the ground up — not just fix it later.

Focuses on what matters with prioritization based on actual risk, impact, and exposure.

Achieves total traceability for compliance, audits, and risk management.

use case
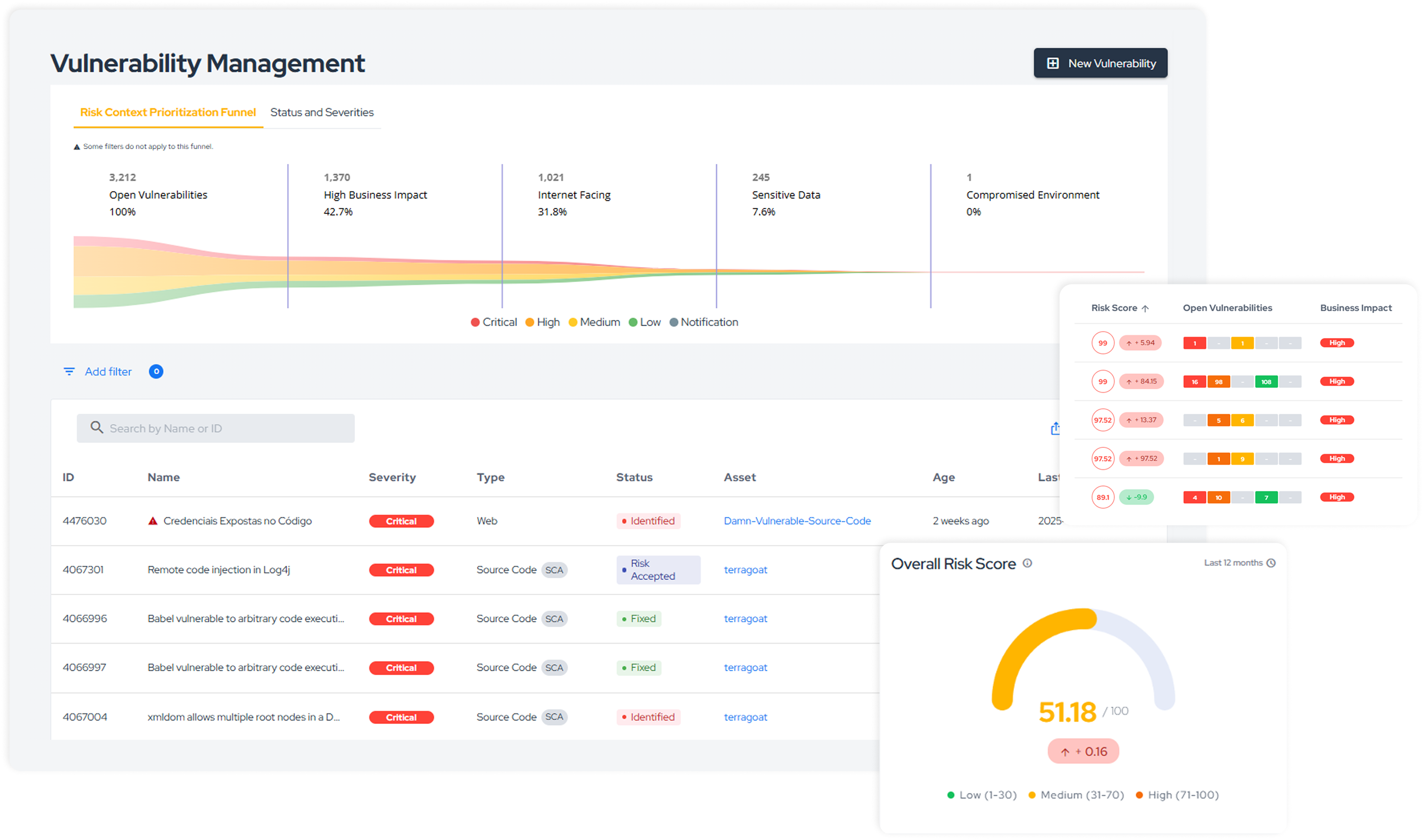
Unify AST, DAST, and SCA/SBOM results, eliminate duplicates, and prioritize remediation based on business impact.

Centralized correlation of vulnerabilities across applications, APIs, and components

Prioritization by exposure and criticality, with clear ownership per team

Evidence and status tracked in an auditable, end-to-end workflow
Explore Conviso Platform solutions and build your AppSec journey
Structured by products and add-ons, the platform allows companies to build their AppSec journey according to real needs, covering everything from secure design to active protection and regulatory compliance.
.png)
Web and API Protection
disponível apenas para usuários do plano Developers
Active edge protection with WAF and global CDN. Blocks real-time attacks while maintaining high performance in production.
Learn more>
AppSec Agent AI
disponível apenas para usuários do plano Developers
AI-powered agent integrated into IDEs, PRs, and pipelines. Detects flaws, suggests fixes, reviews code, and guides developers within their workflow.
Learn more>
.png)
ASPM
disponível apenas para usuários do plano Developers
Centralizes and orchestrates AppSec in a single platform, unifying scanners, prioritizing real risks, and providing end-to-end security visibility.
What is ASPM>

Vuln Intelligence
disponível apenas para usuários do plano Developers
Consolidates findings from multiple sources and applies real risk–based prioritization, reducing noise and accelerating decision-making.
Learn more>

AppSec Squads
disponível apenas para usuários do plano Developers
Specialized squads dedicated to operating and evolving AppSec programs. They structure processes, train teams, and elevate security maturity.
Learn more>

AppScan
disponível apenas para usuários do plano Developers
Automated security testing that transforms findings into traceable vulnerabilities, fully integrated into the development pipeline.
Learn more>

Web and API Scan
disponível apenas para usuários do plano Developers
Dynamic testing (DAST) for detecting vulnerabilities in applications and APIs, with direct integration into remediation workflows.

Threat Modeling
disponível apenas para usuários do plano Developers
Anticipates risks from the design phase, identifying threats and supporting secure decisions in architectures and application flows.
Saiba mais>

Supply Chain
disponível apenas para usuários do plano Developers
Complete visibility into software dependencies and components, with vulnerability analysis and third-party risk control.

OffSec Manager
disponível apenas para usuários do plano Developers
Organizes and tracks offensive testing with prioritized findings, risk visibility, and integration into the development lifecycle.

AppSec Manager
disponível apenas para usuários do plano Developers
Centralizes application security management, consolidates vulnerabilities, and structures workflows for risk control and prioritization.
Saiba mais>

PCI Manager
disponível apenas para usuários do plano Developers
Complete PCI DSS compliance management with structured controls, evidence, and reports for audits and continuous maintenance.
Integrations across the entire development cycle
Conviso Platform eliminates the need to manage multiple tools by centralizing key development, CI/CD, and security solutions in one place.



























Get your questions answered about Conviso Platform
We've selected the most common questions about our ASPM platform to help you understand how it fits into your AppSec program — from tool integration to compliance and maturity support.
Still have questions? Access our detailed documentation or chat with our team.
A Conviso recentemente adquiriu a N-Stalker, uma solução de DAST amplamente reconhecida no mercado global de segurança de aplicações, e a incorporou à sua plataforma. Isso permitiu a realização de análises dinâmicas por meio de uma solução própria.
Além disso, as análises de código estático (SAST) são conduzidas utilizando a engine do Nessus, que está integrada à nossa plataforma.
